Information – Friend or Foe?
Information is both a risk and a resource when thinking about organisational resilience, including business continuity. There are plenty of examples of information losses that have caused major embarrassment, cost a considerable amount of money to resolve and resulted in a loss of trust as well as clients. These have included hacking and cyber attack problems, lost memory devices, leaving files on the train or selling off filing cabinets with records still in them. They even involve being photographed on the way to an important meeting carrying a document the content of which can be easily read from the photographs. Organisations involved have ranged from small business to multi-nationals and public sector bodies. The nature of information as a risk is well publicised. The assessment and treatment of information risks is perhaps less well understood in practice as such losses continue to occur. How well thought through is your information risk strategy? Do you fully understand the nature of this risk and have you treated it properly? No one wants to see his or her organisation’s reputation in the gutter due to the loss of sensitive information, be it commercial or personal.
Information is also a key resource when it comes to operational resilience. Systems and processes are not useable if the information they require is not available in an accurate, up to date and workable form. Often it may take longer to get information, with proven integrity, loaded back onto a system than to recover the hardware itself. The impacts of this fact were experienced by many following banking system failures in the past that resulted in people being shut out of their accounts. The concept of the Recovery Point Objective, the time by which information must be recovered to meet the Recovery Time Objectives of critical processes, is well documented but perhaps less well implemented. If you haven’t gotten into the weeds on this one your resilience strategies may well not deliver as you had hoped.
Then there are those resilience strategies that introduce information risks themselves that did not exist before the business disruption that caused the strategies to be invoked. Take for example home working. How secure is sensitive or personal information, including emails, when this is your selected recovery option? It is not clear that all organisations have assessed this risk and put in place appropriate steps to treat it. The UK Information Commissioner has had recourse, for example, to fine an organisation in the past for information uploaded onto the web accidentally from a home computer during home working.
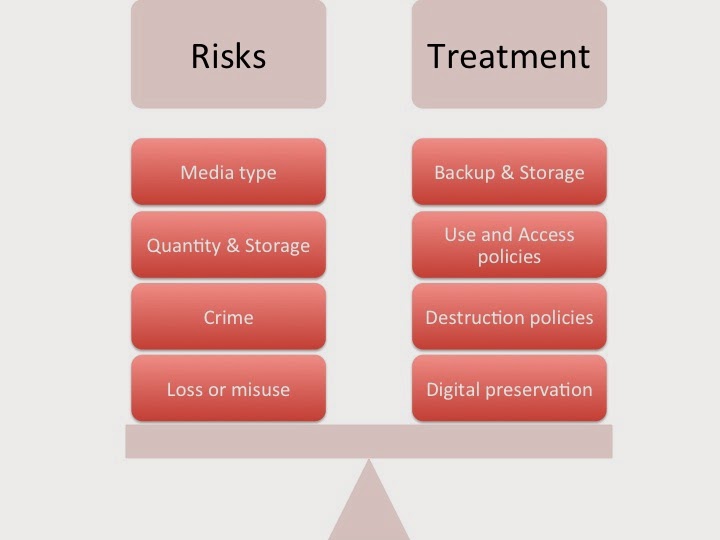
There is legislation to cover information risks with the potential for significant fines and websites that name and shame those found responsible for the loss of personal and sensitive information. Currently the EU is reviewing this legislative framework and the outcomes of this work could significantly strengthen the approach taken with those organisations that compromise such information. Planning for this issue isn’t just about what do to when information may be lost but includes a more careful analysis of what information you gather in the first place, how you store it, for how long you keep it, who you allow to access it and how it can be recovered in time. Added to this is the complication of where information ends up and how people actually access it, sometimes without organisations perhaps being aware. This covers issues as diverse as portable laptops, photocopier memory storage and Bring Your Own Devices (BYOD) such as phones or tablets. The scale of the problem can be considerable.
A key place to start is with an information policy. Such a policy could useful set out the principles by which information is to be governed, from initial collation to storage and use/sharing. It should also include destruction and disposal guidance that can be applied to information no longer of use or technology that is not required or obsolete. Such guidance should also cover the eventuality of the invocation of recovery strategies as well as how damaged or irreparable equipment that could hold information is to be safely managed. You can find out much more about this issue at the ICO’s website. Go have a look and educate yourself on this risk and resource.
